Splunk

Version: 1.3 Updated: Sep 18, 2025
Search and send events with Splunk.
Actions
- Search Into Events Splunk (Enrichment) - Search Splunk events.
- Send Splunk Events (Notification) - Send an event to Splunk.
- Splunk Events Daemon (Daemon) - Daemon to gather new Splunk events.
- Splunk Alerts Daemon (Daemon) - Daemon to gather new Splunk alerts.
- Update Notable Event (Notification) - Update a notable (important) event in Splunk.
Notes
- Important: Change the line
\_indextime>0000000000to indicate the time in Epoch format you wish to begin creating incidents from in the Splunk Events Daemon action. - Only default fields, such as
[].\_raw,[].host, and[].sourceare included in the Search Into Splunk Events and Splunk Events Daemon actions.
To use any custom fields from Splunk within Cloud SOAR, make sure they are added to these action files.
Configure Splunk in Automation Service and Cloud SOAR
Before you can use this automation integration, you must configure its authentication settings so that the product you're integrating with can communicate with Sumo Logic. For general guidance, see Configure Authentication for Automation Integrations.
How to open the integration's configuration dialog
- Access App Central and install the integration. (You can configure at installation, or after installation with the following steps.)
- Go to the Integrations page.
Classic UI. In the main Sumo Logic menu, select Automation and then select Integrations in the left nav bar.
New UI. In the main Sumo Logic menu, select Automation > Integrations. You can also click the Go To... menu at the top of the screen and select Integrations. - Select the installed integration.
- Hover over the resource name and click the Edit button that appears.
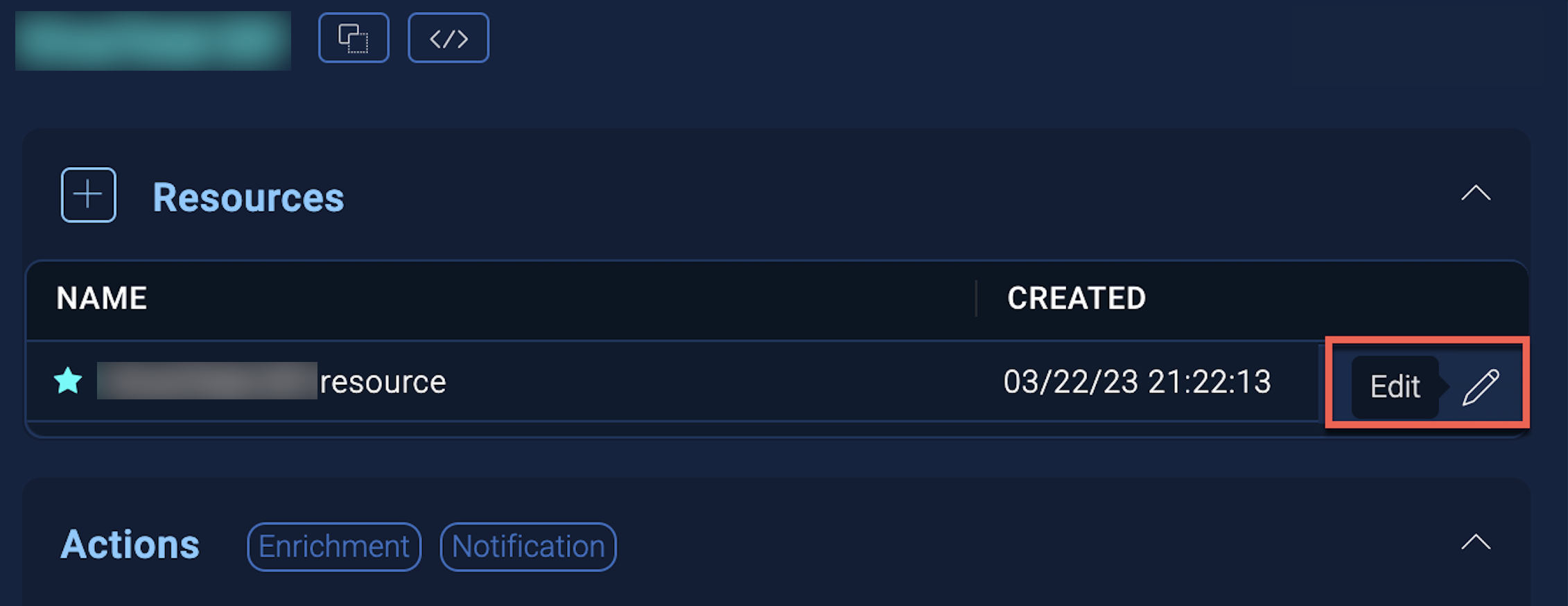
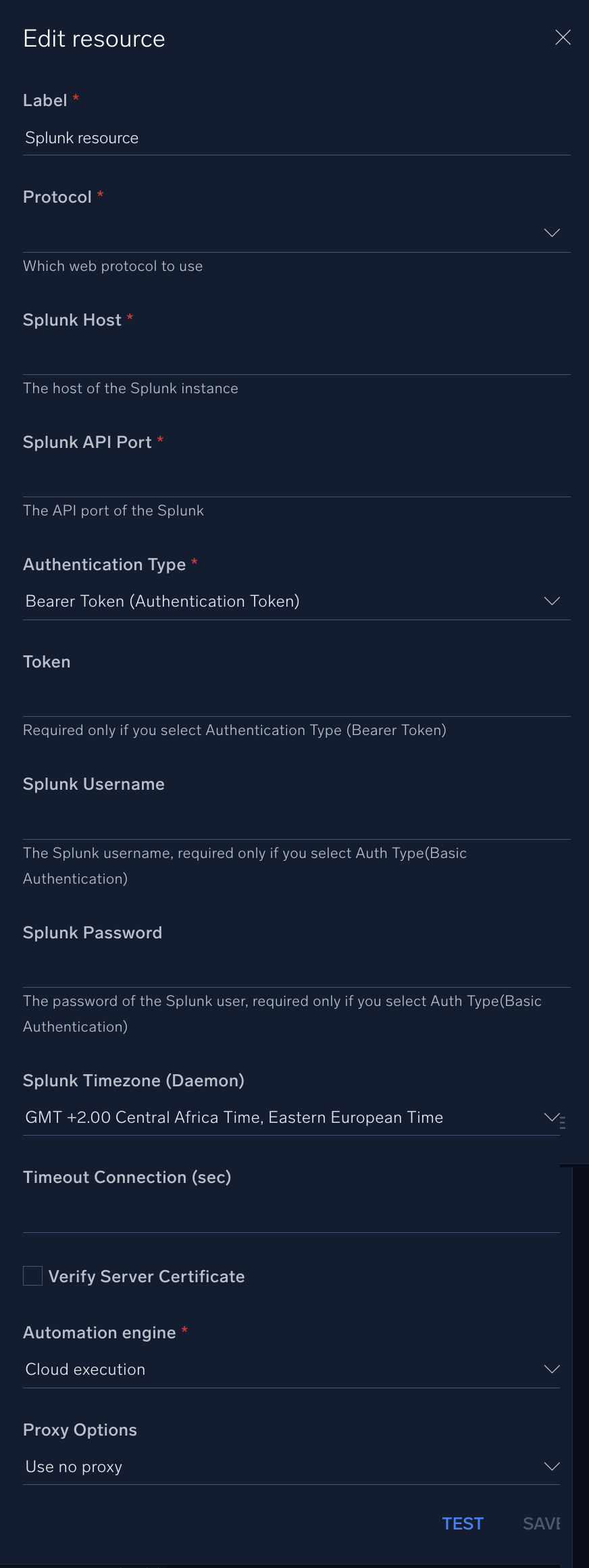
In the configuration dialog, enter information from the product you're integrating with. When done, click TEST to test the configuration, and click SAVE to save the configuration:
-
Label. Enter the name you want to use for the resource.
-
Protocol. Enter your protocol:
- HTTP
- HTTPS
-
Splunk Host. Enter the hostname of your Splunk instance.
-
Splunk API Port. Enter your Splunk API port, for example,
8089. -
Authentication Type. Select the authentication type:
- Username and Password (Basic Authentication)
- Bearer Token (Authentication Token)
-
Token. Enter your Splunk token. Required only if you selected Bearer Token (Authentication Token).
-
Splunk Username. Enter the username of a Splunk admin user authorized to authenticate the integration. Required only if you selected Username and Password (Basic Authentication)
-
Splunk Password. Enter the password for the Splunk user. Required only if you selected Username and Password (Basic Authentication)
-
Splunk Timezone (Daemon). Select your timezone.
-
Connection Timeout (s). Set the maximum amount of time the integration will wait for a server's response before terminating the connection. Enter the connection timeout time in seconds (for example,
180). -
Verify Server Certificate. Select to validate the server’s SSL certificate.
-
Automation Engine. Select Cloud execution for this certified integration. Select a bridge option only for a custom integration. See Cloud or Bridge execution.
-
Proxy Options. Select whether to use a proxy. (Applies only if the automation engine uses a bridge instead of cloud execution.)
- Use no proxy. Communication runs on the bridge and does not use a proxy.
- Use default proxy. Use the default proxy for the bridge set up as described in Using a proxy.
- Use different proxy. Use your own proxy service. Provide the proxy URL and port number.
For information about Splunk, see Splunk documentation.
Change Log
- May 5, 2019 - First upload
- June 4, 2019 - Search Into Events Daemon updated
- June 19, 2019 - Search Into Events Daemon updated
- December 19, 2019 - Splunk Alerts Daemon Added
- February 21, 2020 - Updated Splunk Events Daemon
- March 9, 2021 - New action added
- March 25, 2021 - Updated authentication (Authentication Token and Basic Authentication available)
- July 13, 2023 (v1.2)
- Updated the integration with Environmental Variables
- Integration renamed from Splunk OIF to Splunk
- Changed fields visibility
- Changed Daemon compatibility (Splunk Alerts Daemon)
- September 18, 2025 (v1.3)
- Improved timezone handling in alert queries.
- Improved URL encoding to handle reserved characters.